Social Media
How much contact and personal information do you give away in your LinkedIn profile and who can see it? Here’s why less may be more.
16 Nov 2023 • , 4 min. read

Several friends recently asked me how cybercriminals could gain access to their contact data, especially their mobile phone numbers and email addresses. I basically told them that there are several methods that criminals can use to gather such information. One common method involves data stolen in breaches that have impacted online platforms and their users over the years. This has ultimately given rise to a thriving market for stolen personal data, both on the dark web and increasingly also on the ‘surface web’.
But there is another possible scenario that could enable anybody with ill intentions to compile their own “contact lists” packed with up-to-date and valuable data. Enter LinkedIn, the world’s largest social network for professionals, where criminals have previously gathered publicly available information on millions of its users with relative ease, including full names, phone numbers, email addresses, workplace information, and more.
This wealth of available information has to do with the platform’s very nature. LinkedIn users often choose, and understandably so, to make their information public, including their personal or professional contact details. An unintended consequence of this is that criminals don’t need to rely on information that may have been stolen or leaked years ago and some of which may no longer even be up to date and accurate.
Instead, they can leverage web scrapers to collect all available information about their potential targets. They can then go on to commit identity theft or target the users’ employers with business email compromise (BEC) scams or other social engineering attacks.
Among other things, web scrapers can:
- Create a list of a company’s employees
Here, the offender only needs to configure the data collection software to access the “People” tab of the target company, resulting in an up-to-date list of employees. Obviously LinkedIn users tend to keep their profiles up-to-date with their current job information.
- Compile a list of “supply chain targets” related to a company
Some criminals may go further and review interactions on the company’s social media posts to identify potential suppliers and partners, thus obtaining new high-priority targets or potential avenues to attack the primary target’s supply chain.
What do you choose to publish?
In many cases, people’s information may be either publicly accessible or be only visible to those within a user’s network of direct connections. The amount of available information may also vary:
- LinkedIn profiles that don’t reveal any contact data outside the platform
By choosing not to share any contact information outside the platform and your direct connections, you significantly limit the amount of information that criminals can gather on you. Your full name, job title, and your company’s geographical location will still be visible, of course.
- LinkedIn profiles that make their email address public
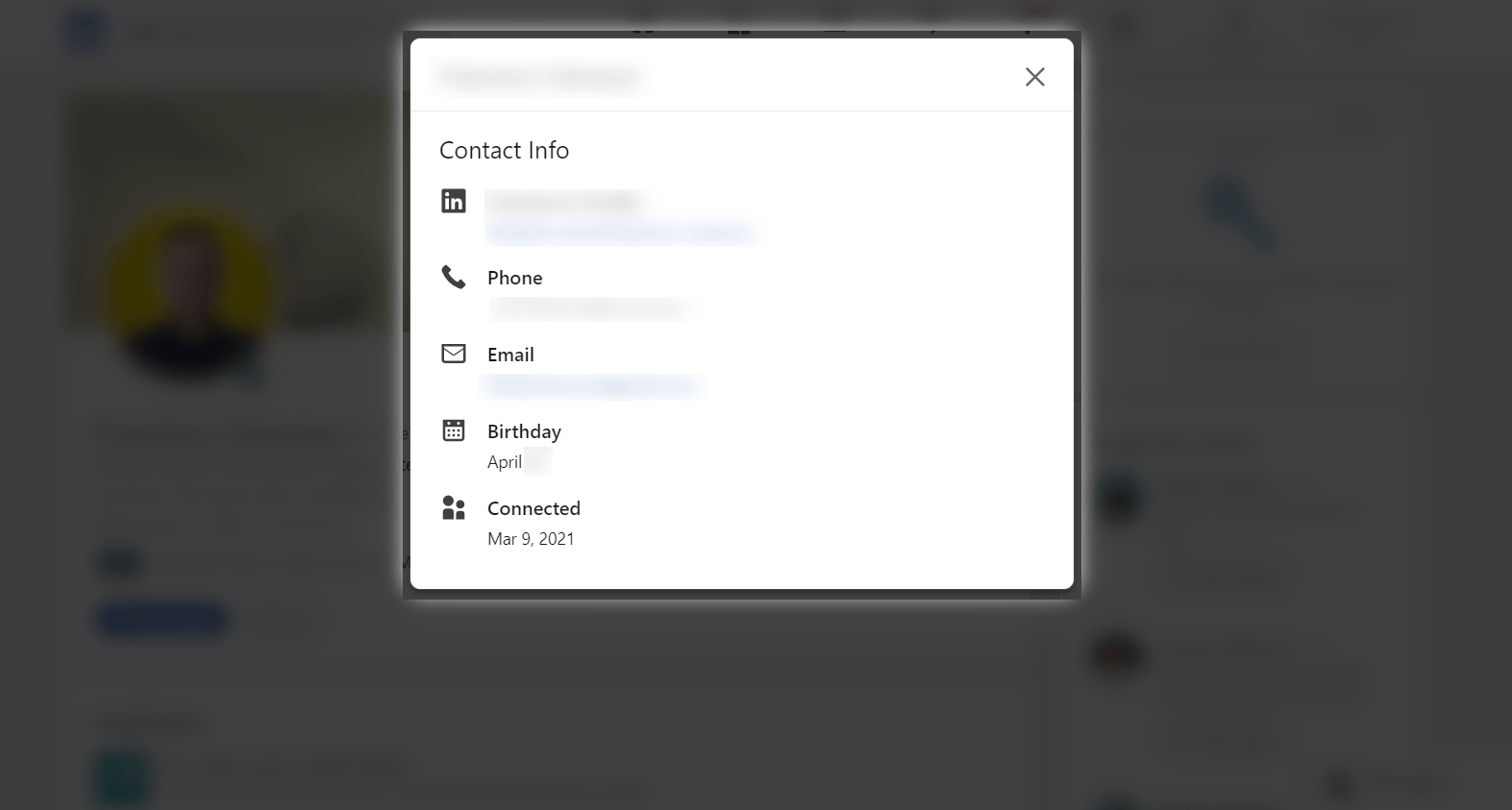
While LinkedIn users often share their personal contact information, some may also divulge their current corporate email addresses. Either way, this could allow malicious individuals to engage in more targeted interactions with their victims, as well as clue them in on the typical email format used by the company (although obviously this is far from the only easy way of acquiring that information).
- LinkedIn profiles that make phone numbers public
Some people may choose to divulge their phone number, for example in the hopes that recruiters and employers will have an easier time contacting them for interviews or perhaps that this will facilitate easy communication with potential business contacts or clients. Much like with emails, however, this can lead to fraudulent calls, messages (aka smishing), potential data misuse and privacy breaches.
Mitigating risks
The very nature of social networking, and on any platform, enables criminals to access some of our data online. However, there are several measures you can take to prevent criminals from accessing your most valuable information on LinkedIn:
- Configure your LinkedIn privacy settings
LinkedIn offers various options to limit the information available to those outside your circle connections. You should apply the same kinds of measures on other social media sites, but it may be particularly important on LinkedIn. Refer to our article on how to use LinkedIn safely, where we covered this and other aspects of staying safe on the platform.
- Limit the amount of information in your profile
As a social media platform, LinkedIn provides tools for networking and job seeking, but consider prioritizing contact through the platform itself and avoid sharing external contact data.
- Don’t accept connection requests indiscriminately
There are many bots and fake profiles on the platform, so review the legitimacy of each connection request before accepting them. Be also cautious when it comes to answering messages on LinkedIn, especially if they request your personal information or send you links or attachments.
- Review the list of your connections regularly
Given the prevalence of fake profiles, review your list of connections regularly and remove contacts that appear suspicious.
- Be cautious about broadcasting your profile updates
Perhaps you don’t always need to update your job status as soon as your situation changes and broadcast it to the world. Criminals could monitor such changes and may exploit your limited knowledge of the new work environment or situation to send you malicious emails or text messages.
To reiterate, make sure to review your profile’s privacy settings to control who can see your contact information and so minimize the risk of unwanted contact or privacy breaches. LinkedIn is a valuable social media platform, but it’s crucial to strike a balance between networking and safeguarding your personal information.
RELATED READING:
A step-by-step guide to enjoying LinkedIn safely
Fake friends and followers on social media – and how to spot them
Social media in the workplace: Cybersecurity dos and don’ts for employees

